Security 2016: Taking back the network

When you think of security issues, you might think about a room full of gamers who've gone rogue as hackers. That might be a one-off group. You might think of Anonymous--a loosely organized group of geographically diverse hackers who collect enemies faster than ISIS does. Or do you 'get real' for a minute and think about the people sitting around you in your cubicle farm? If you thought about your cubicle clone...umm...coworkers, you're on the right track. Sure there are hacker groups out there and some of them are even 'state' sponsored, but they aren't as a big a threat as the guy who begrudgingly shares a network printer with you.
Spiceworks, the Austin-based purveyor of fine free software, special services, and the best IT community on the planet conducted a security survey to find out what IT pros are worried about and what they're going to do about it. The survey results compiled from the responses of close to 200 IT pros spread throughout North America and EMEA, sheds some interesting light into the darkness of Shadow IT, hacking, and network security.
First, look at what the respondents thought of the questions of top security concerns. In other words, "Which threats are you most concerned about?" The responses show percentages of IT pros who either are "very" or "extremely" concerned.
- Malware - 54 percent
- Ransomware - 53 percent
- Phishing - 46 percent
- Data leaks/theft - 39 percent
- Spyware - 38 percent
- Password breach - 37 percent
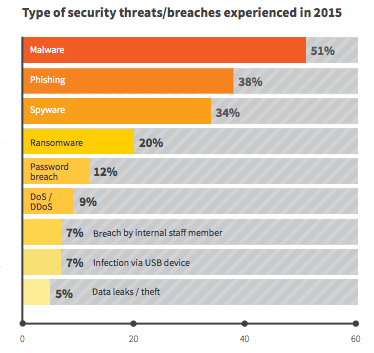
As you can see from the above number of security concerns vs. actual threats and breaches experienced by companies in 2015, IT pros are appropriately concerned about actual threats. The ones that stand out from the pack are Ransomware and password breaches. However, I believe that IT professionals are still appropriately concerned, not because of the raw numbers, but because of the size and the extent of the seriousness of these two breaches. The number don't reflect the time, money, and data lost due to those breaches, which in my mind explains the disparity in the numbers.
Where are the threats, you ask? If you think about it, when everyone travelled into an office every day, sat down, powered on the computer, worked, powered off the computer, and went home--threats were somewhat limited to what someone could carry in on a floppy or make you execute in an email message. These days, we're mobilized: laptops, tablets, smartphones, and wearables make our data and our gadgetry vulnerable to theft, attacks, and malware.
The survey respondents view the "where" in the following percentages:
- Laptops - 81 percent
- Desktops - 73 percent
- Smartphones - 70 percent
- Tablets - 62 percent
You might believe that BYOD is the culprit in these very high numbers, but it isn't. These numbers apply to both company-owned and BYOD hardware. Other notable "where" weak points are:
- Servers - 49 percent
- IoT devices - 49 percent
- Wireless access points - 47 percent
- Routers and switches - 38 percent
These "where" results are exactly in line with where I see weaknesses and threats. Any device that travels from the office to unknown and uncontrolled destinations and back again are going to be pathways for threats. Once inside the network, those threats can spread to other computers and if attackers gain full control of a system, any network-connected device is at risk.
Approximately half of the respondents (48 percent) report that Shadow IT poses a significant threat to corporate security. I'm actually surprised that the number isn't higher. Most threats, whether they originate with those who ignore protocol, who maliciously attack from within, or who unwittingly breach, come from inside corporate walls.
The graphic below illustrates how significant the perceived threat from insiders is at 36 percent of the respondents being concerned about "rogue" employees.
The reason I believe the number should be higher is because of the employee who doesn't take enough precaution, who doesn't think about security, who answers those Nigerian Prince emails to launder money, or who answer every question from a convincing person who wants to help them fix their errant computer.
So, in the "What are you going to do about it" department, IT pros have a multifaceted plan that includes user education, regular updates, better monitoring, policy enforcement, regular updates, and BYOD restrictions. The last one surprises me. BYOD doesn't significantly increase the threat, but that's an argument not worth having. It's about as effective as getting someone to change political party affiliation.
The two most important actions that a company could take are user education and regular updates to hardware and software, with user education being the more powerful deterrent against all types of threats.
And now for the validation of my personal rant about insider threats, please enjoy the graphic below that illustrates the top security challenges for IT.
Although it's pretty typical for IT folk to blame users and management for all their problems, they might have something here. Part of the problem is though that end users see IT people as the nerds and geeks that they have to deal with to get what they need and management sees IT as pure overhead--a cost to the bottom line. It's no wonder that we often feel like we're caught in the middle, because we are. IT is the dog that gets kicked when things go wrong and a passing "Good boy" when things go really right.
So, in 2016, where are IT pros going to spend the money? Here are the top five answers.
- Intrusion detection - 36 percent
- Content filtering - 32 percent
- Firewalls - 30 percent
- VPN - 30 percent
- Anti-virus - 29 percent
But nowhere in the top 16 is user security training. Training is another overhead--a cost. But what is the cost of a significant data breach? I can't answer that for every case, but I can tell you that user training is about ten percent of the cost of a pretty insignificant data breach. You do the math.
Where are you going to spend your 2016 security budget? Do these numbers line up with your plans? What do you think of end user education as a deterrent? Use the comments section and sound off.