Mobile Chrome, Safari, and Firefox failed to show phishing warnings for more than a year

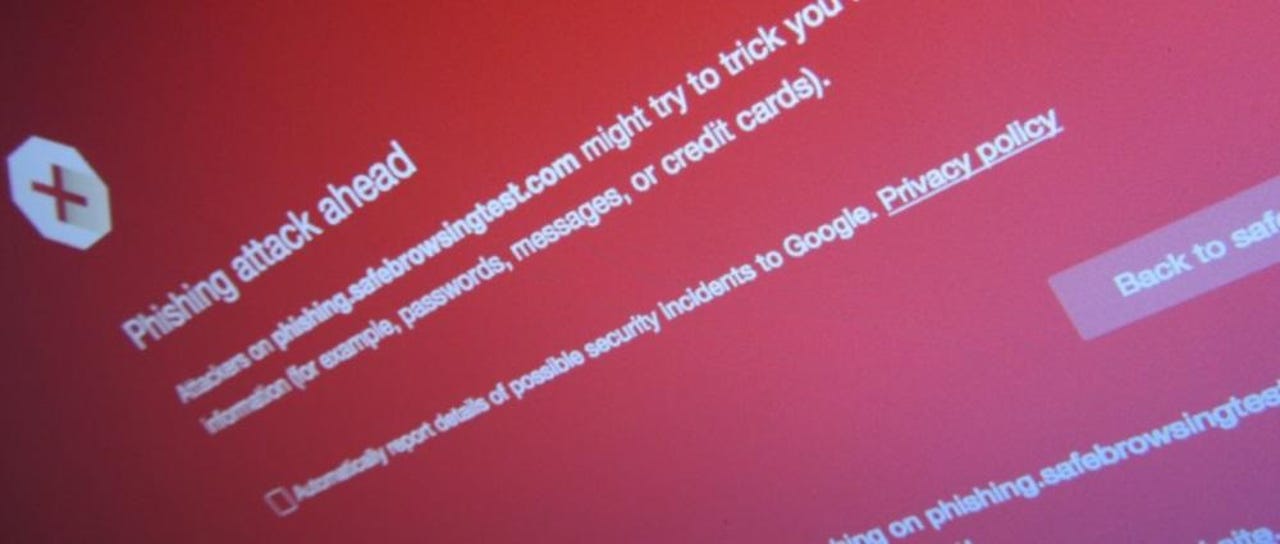
For more than a year, mobile browsers like Google Chrome, Firefox, and Safari failed to show any phishing warnings to users, according to a research paper published this week.
"We identified a gaping hole in the protection of top mobile web browsers," the research team said.
"Shockingly, mobile Chrome, Safari, and Firefox failed to show any blacklist warnings between mid-2017 and late 2018 despite the presence of security settings that implied blacklist protection."
The issue only impacted mobile browsers that used the Google Safe Browsing link blacklisting technology.
The research team -- consisting of academics from Arizona State University and PayPal staff -- notified Google of the problem, and the issue was fixed in late 2018.
"Following our disclosure, we learned that the inconsistency in mobile GSB blacklisting was due to the transition to a new mobile API designed to optimize data usage, which ultimately did not function as intended," researchers said.
PhishFarm research project
The discovery of this significant security bug came during an academic research project named PhishFarm, started in early 2017.
During PhishFarm, researchers created and deployed 2,380 phishing pages mimicking the PayPal login page. Researchers didn't measure how fast their URLs landed on URL blacklists. This type of research has been done in the past.
Instead, they focused on deploying phishing pages with "cloaking techniques" aimed at tricking URL blacklist technologies and then recording the time it took for these "cloaked" phishing pages to land on lists of "dangerous sites" -- or if they landed at all.
For PhishFarm, researchers tested URL blacklists such as Google Safe Browsing, Microsoft SmartScreen, and those managed by US-CERT, the Anti-Phishing Working Group, PayPal, PhishTank, Netcraft, WebSense, McAfee, and ESET.
Further, the research team's phishing pages also used six (actually five) cloaking techniques researchers said they've seen used by phishing kits in the real-world:
- Cloak A - allow all users to view the phishing page, aka a no-cloak mode used as a baseline for all detections
- Cloak B - allow only users from mobile devices
- Cloak C - allow only US users from desktop devices
- Cloak D - allow only non-US users from desktop devices
- Cloak E - block visitors from IP addresses known to be associated with security vendors
- Cloak F - allow only browsers where JavaScript is enabled
"We found that simple cloaking techniques representative of real-world attacks- including those based on geolocation, device type, or JavaScript- were effective in reducing the likelihood of blacklisting by over 55% on average," researchers said.
Results varied per URL blacklists and cloaking technique [check graphs at the end of the research paper], but the thing that stood out during their research was that cloaks A, E, and F had zero detections on mobile browsers that were using Google's Safe Browsing URL blacklist.
When researchers repeated their tests in mid-2018, they got the same results, at which point they realized that Google's Safe Browsing technology was not working as intended on mobile devices. [Cloak A was effectively a "no cloak," meaning that Safe Browsing was not alerting users about any phishing pages, even if they used cloaking technologies or not -- effectively not working at all].
The issue was eventually fixed by the end of 2018, researchers said.
More on this research can be found in a paper entitled "PhishFarm: A Scalable Framework for Measuring the Effectiveness of Evasion Techniques Against Browser Phishing Blacklists," available for download in PDF format from here, here, or here.
Closing out @IEEESSP #sp19 Adam Oest presents “PhishFarm: A Scalable Framework for Measuring the Effectiveness of Evasion Techniques Against Browser Phishing Blacklists” pic.twitter.com/gTdQYYCIhX
— Elissa Redmiles (@eredmil1) May 22, 2019
Say hello to the early days of web browsers
Related cybersecurity coverage:
- Google research: Most hacker-for-hire services are frauds
- Android and iOS devices impacted by new sensor calibration attack
- UK says it warned 16 NATO allies of Russian hacking activities
- Root account misconfigurations found in 20% of top 1,000 Docker containers
- Some Elasticsearch security features are now free for everyone
- Microsoft releases new version of Attack Surface Analyzer utility
- Why cybersecurity pros want to share information to combat threats TechRepublic
- Google takes aim at imposter websites with new Chrome warning CNET