Mirai DNS Water Torture finance sector attack dominated Q1: Akamai

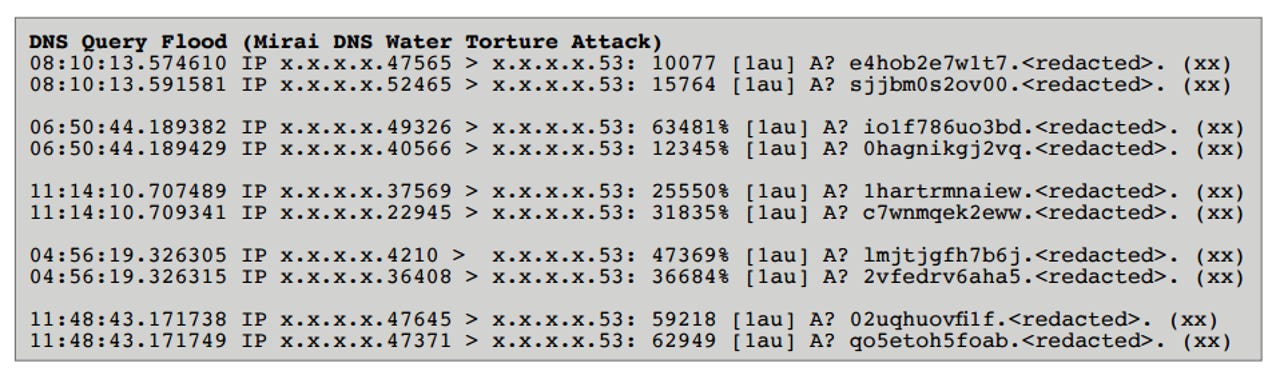
Mirai DNS Water Torture attack payload, with target domain names redacted
Mirai DNS Water Torture distributed denial of service (DDoS) attacks dominated the first quarter of 2017, a report from Akamai has found.
According to Akamai's State of the Internet/security Q1 2017 report, Water Torture attacks using this DNS query vector were first observed on January 11, 2017, targeting several of the company's customers in the financial services industry.
The attack activity began with five consecutive days of attacks -- when one of three DNS servers received 14 Mbps of attack traffic -- followed by a four-day reprieve before concluding with a final attack on January 20, 2017.
Water Torture follows normal DNS recursion paths, Akamai explained, and as a result, the attacker cannot select a specific IP address at the target site.
"Although DNS query attacks are not as common as DNS reflection attacks, this DNS query flood can potentially cause more damage than current DNS reflection attacks," Akamai wrote. "If a targeted DNS server is unprepared for a sustained flood of queries with high packet rates."
The Mirai DNS query flood does not use reflection or spoofing techniques, nor does it allow attackers to specify a target IP, rather it accepts a domain name as the target for a DNS cache-busting flood.
A randomised 12-character alphanumeric subdomain is prepended to the target domain and the attacking bots send their queries to their locally-configured DNS servers, which are typically DNS servers at local ISPs.
According to Akamai, the randomised subdomain is present to ensure that no intermediate recursive DNS server would have the response for that name cached locally, but, since the response cannot be cached, every query follows the usual path until it reaches an authoritative DNS server, which is the real target of the attack.
As a result, Water Torture can lead to a denial of service for legitimate users as each query ties up memory and processor cycles, preventing the target from processing legitimate traffic.
"If our analysis of Q1 tells us anything, it's that risks to the internet and to targeted industry sectors remain and continue to evolve," said Martin McKeay, senior security advocate at Akamai.
"Use cases for botnets like Mirai have continued to advance and change, with attackers increasingly integrating Internet of Things vulnerabilities into the fabric of DDoS botnets and malware."
According to McKeay, it is a short-sighted approach to think of Mirai as the only threat, as with the release of the source code, any aspect of Mirai could be incorporated into other botnets.
"Even without adding Mirai's capabilities, there is evidence that botnet families like BillGates, elknot, and XOR have been mutating to take advantage of the changing landscape," he added.
The report also found there was a 35 percent year-over-year increase in total web application attacks from Q1 2016, as well as a 57 percent increase in attacks originating from the United States -- which is the top attack source country.
There was a 30 percent decrease in total DDoS attacks; a 28 percent decrease in infrastructure layer three and four attacks; a 19 percent decrease in reflection-based attacks; and an 89 percent decrease in attacks greater than 100 Gbps over quarter one last year.
Akamai compiled its latest report [PDF] from analysis and research based on data from its global infrastructure and routed DDoS solution.