Android security report: Google aims to clean up 'unwanted software' in 2017

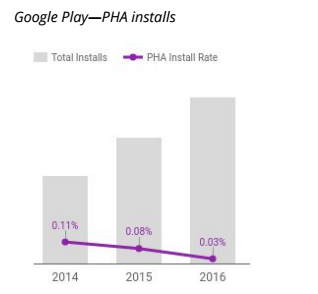
Tackling malware like the mobile trojan Ghost Push, Google has steadily reduced the overall install rate of "potentially harmful apps" (PHAs) on Android phones from 2014 through 2016, the company reported in its 2016 Android Security Year in Review.
"The decrease in PHA install rate is primarily due to campaigns to clean up apps in the Ghost Push family," Google said. The chart to the left represents the year-over-year trends for PHA install rates relative to total installs for 2014 to 2016.
At the same time, Google is acknowledging a distinct risk for "unwanted software" on Android phones -- a problem it's more aggressively addressing in the year head. From the report:
Google uses the concept of "unwanted software" (UwS) as a way to deal with applications that are not strictly considered malware, but are generally harmful to the software ecosystem. In 2016, Android took a similar approach with mobile, introducing Mobile Unwanted Software (MUwS).
This type of app has long been prohibited by Google Play's policies--but even outside of Google Play it is harmful to the Android ecosystem and unwanted by most users. An example of common MUwS behavior is overly aggressive collecting of device identifiers or other metadata.
In 2016, there was a rise in legitimate developers collecting more information about users and devices for analytics and advertising purposes, Google said. Correspondingly, there's been an increase in the installation of apps that include of third-party SDKs that collect user identifying information.
"This trend is one of the reasons that we introduced the MUwS classification and are working to enforce new policies for MUwS in 2017," the report said.
In 2016, MUwS were defined as apps that -- without user consent -- collected information about installed applications, information about third-party accounts, or names of files on the device. Google expects to classify more actions as MUwS in 2017.
The installation base of legitimate apps that violate data-collection guidelines is much larger than the installation base of PHAs, Google noted. By working with developers, Google and its partners removed data-collection code from applications used by "tens of millions of users" in 2016, it said.
Meanwhile, to hunt down traditional PHAs, Google in 2016 focused on enhancing machine learning and analytical capabilities, building new security features into Android 7.0 Nougat, and collaborating with other members of the Android ecosystem.
There are more than 1.4 billion Android users, the report noted. Since Google started measuring Android security in 2014, it's found that on average less than 1 percent of devices have PHAs installed.
As Google has noted in previous years, there's a much bigger risk in downloading apps outside of Google Play. PHAs accounted for 0.16 percent of all apps published to Google Play in 2016. A user was 10 times more likely to download a PHA from outside of Google Play in 2016.
Overall, the rate of PHA installs, both inside and outside of Google Play, dropped in 2016 compared to 2015, "primarily as a result of improved detection of large families such as Ghost Push," the report said. By Q4 2016, fewer than 0.71 percent of devices had PHAs installed.
The majority of those were trojans. Other forms of PHAs included hostile downloaders, phishing apps, backdoors, SMS fraud, and toll fraud.
The report laid out the systems Google uses to address threats, including app analyzers that review applications for unsafe behavior. Verify Apps, for instance, regularly checks users' devices for PHAs. In late 2016, it was updated to automatically block install attempts initiated by an installed PHA.
Using data from Verify Apps, Google in 2016 began tracking devices that were dead or insecure after downloading apps -- this helped Google identify members of the HummingBad, Ghost Push, and Gooligan PHA families. Also last year, Google started focusing on apps from outside of Google Play that root devices without user consent. The company built a machine learning model to separate malicious and user-intended rooting apps.
"We believe that advances in machine learning and automation can help reduce PHA rates significantly in 2017, both inside and outside of Google Play," the report said.
Google also took new steps in 2016 to work with third-party developers, such as releasing the Safe Browsing API. This allowed third-party apps to easily use to use Safe Browsing's database of known harmful URLs.
To reach the broader Android ecosystem, Google released monthly security bulletins and patches to the Android Open Source Project (AOSP). By working with device manufacturers, SOC providers and telecoms, more than half of the top 50 Android devices had an available security patch by Q4 2016.
VIDEO: Your Android phone may have malicious ghost apps installed