ACSC comfortable with enforcing JavaScript on site visitors

The Australian Cyber Security Centre (ACSC) has taken the step of blocking access to its website for regular desktop browsers that have JavaScript disabled.
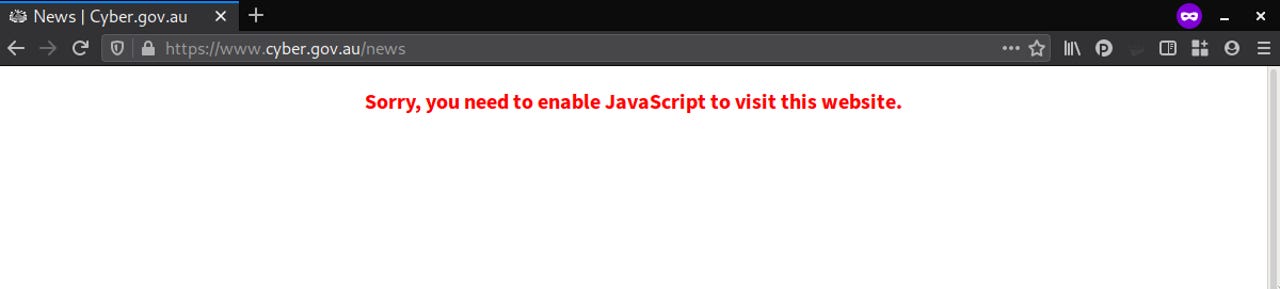
If a user heads to cyber.gov.au today without JavaScript enabled, they will be handed the message, "Sorry, you need to enable JavaScript to visit this website", and no more.
Ironically, as ZDNet tested the site and as shown below, it was found that while the notice was shown to users of text-based browser lynx, the content of the page was still served up to them.
The end result is for the extreme security-minded or resource-constrained users, that they get more functionality browsing the Australian government's official cyber communications channel from the command line, than a desktop browser without JavaScript.
After reaching out for an explanation of the situation, the ACSC told ZDNet that its use of JavaScipt was consistent with the advice in the Australian Signals Directorate's Strategies to Mitigate Cyber Security Incidents Mitigation Details document.
"Disallowing javascript [sic], except for whitelisted websites, is ideal though challenging due to the large number of websites that require such functionality for legitimate purposes, and is difficult to implement in a large scale deployment," the only paragraph mentioning JavaScript in the document states.
It would appear ACSC is not helping the ASD's ideal.
"The cyber.gov.au website uses JavaScript for legitimate purposes, for features such as the 'ReportCyber' interactive application used to report cyber incidents," the ACSC also said.
Although we did not test it, the take away would seem to be that if you were deep in a concrete bunker data centre that doubled as a mobile phone reception blocker and wanted to report a cyber incident from a server, one would need to spark up a full desktop experience.
In September, ACSC said it receives reports of cybercrime once every 10 minutes.
A month later at Senate Estimates, the ACSC fessed up to the worst kept secret in Australian cybersecurity circles -- that it had two speakers dumped from CyberCon in early October.
"I made that decision," ACSC chief Rachel Noble told Senate Estimates at the time.
"The advice that I made the decision on, was a proposal for Dr Dreyfus and Mr Drake to ... have a panel with Edward Snowden that was the first proposal. At that point my judgement was based on, I guess, a reputation of all of those speakers that they are known public advocates for unauthorised disclosure or the leaking of classified information outside of legitimate whistleblowing or lawful whistleblowing schemes."
Noble added the talks were not "consistent with the objectives of the conference which was actually about cybersecurity and helping Australians raise their awareness and technical knowledge about cybersecurity issues", and could express views not in line with Australian law, processes, and values.
It's not often lynx provides a better browsing experience, but the ACSC has made it so.
Related Coverage
ACSC confirms it killed off CyberCon whistleblower talks
Head of the ACSC Rachel Noble says all speakers were 'known public advocates for unauthorised disclosure'.
Telstra calls for Australia to undergo national cyber stocktake
Telco also wants repeat of 2016 ASX 100 cyber check survey.
Renewed calls for dedicated Australian cyber minister and cyber leadership
Australia's cybersecurity is too important to struggle along with part-time attention, say submitters to the Cyber Security Strategy 2020. The public no longer trusts the government's computer skills.
Parliament House hack report reveals poor password practices
It took eight days to flush February's cyber attackers from Australia's parliamentary network. A procedure to authenticate staff asking to reset their boss' passwords only came another week later.
The 10 most important cyberattacks of the decade (TechRepublic)
After a number of devastating breaches and hacks, the sheer size of data lost is no longer the only indicator of severity.